Effortless Background Removal with AI Ease: A Revolutionary Free Online Tool
Say goodbye to complicated background removal! AI Ease offers a FREE, lightning-fast, and easy tool to edit images like a pro. No sign-up, no hassle—just stunning results!

Say goodbye to complicated background removal! AI Ease offers a FREE, lightning-fast, and easy tool to edit images like a pro. No sign-up, no hassle—just stunning results!
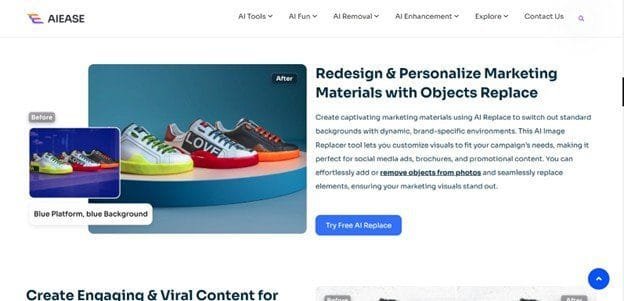
Want to transform your photos in seconds? Discover The Best AI Replacer Online Free! Easily swap objects, change backgrounds, and create stunning images—no skills required! Try it now!

Discover how “Improving Decision-Making in Manufacturing Through Real-Time Data” can transform your production line, cut costs, and skyrocket efficiency. Don’t get left behind!

Want to skyrocket your sales and enhance customer experience? Discover how Chatbots for E-commerce Businesses are transforming online shopping with 24/7 support, personalized recommendations, and more!

Struggling to find the perfect hairstyle? Discover how your face shape impacts your look and try on different styles for FREE with AI Ease. Find your ideal cut today—no salon required!

Unleash your creativity with AI Ease Free AI Face Swapper! Swap faces with celebrities, memes, and friends instantly—100% free, fun, and totally addictive! Try it now!
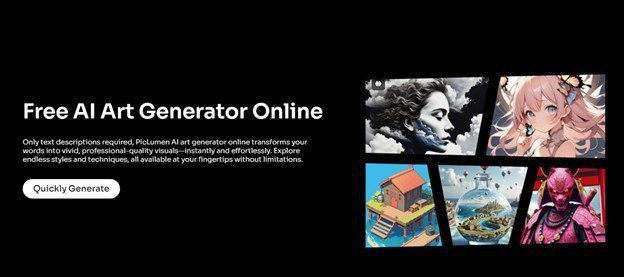
Discover PicLumen: the AI art generator that transforms words into breathtaking visuals! From retro synthwave to serene realism, explore endless styles and unleash your creativity!
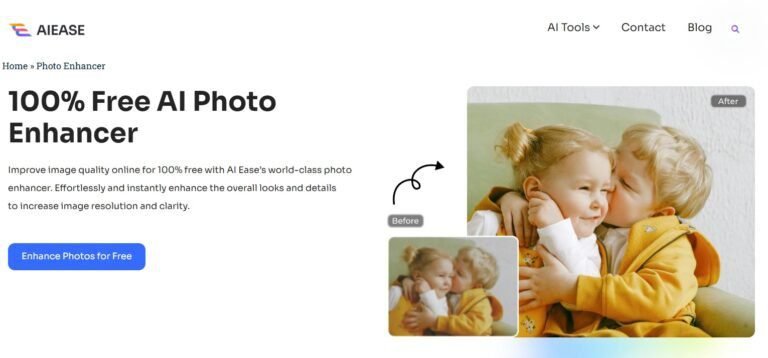
Blurry photos ruining your shots? Learn How to Unblur the Image with AI Ease! Discover pro tips and AI tools that make image sharpening a breeze. Click to get crystal-clear results!
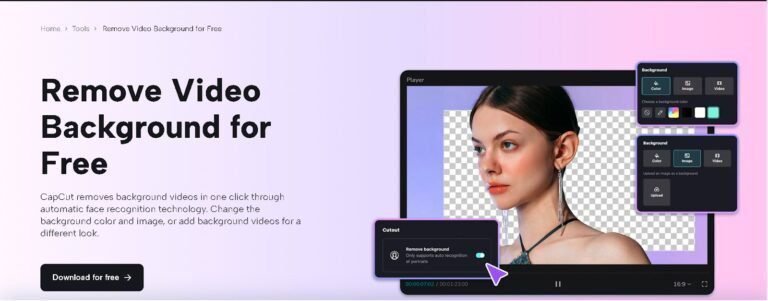
Want pro-quality videos that stand out? Discover why using a video background remover is the game-changer you need! Boost engagement, creativity, and make every shot look stunning!

Ever wanted to swap faces with a celeb or turn into your favorite character? Discover How to Multiple Swap in Photo Online with AI Ease’s AI Face Swapper—it’s free, fun, and instant!
End of content
End of content