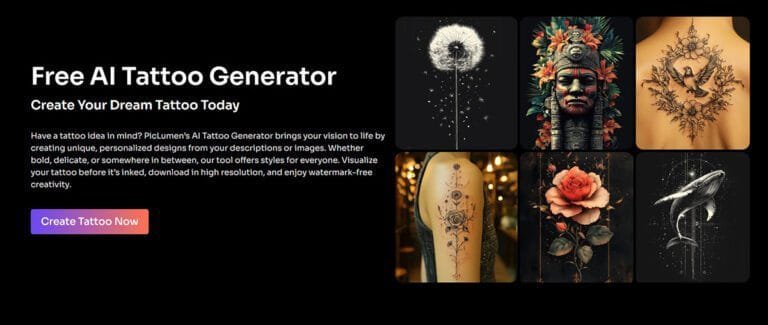
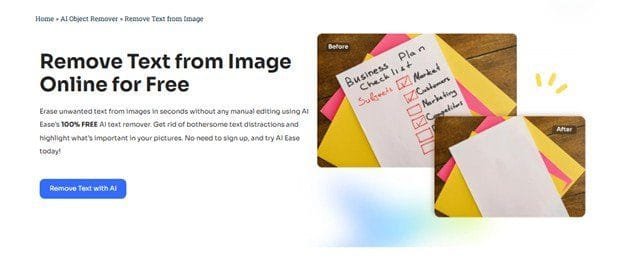
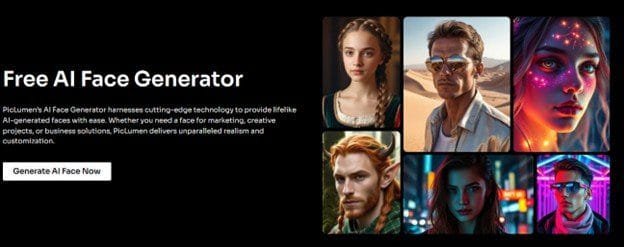
Instantly transform your photos with our AI-powered image upscale and enlarger.
Discover the magic of our AI-powered image upscale and enlarger! Transform low-res photos into stunning HD masterpieces instantly—100% free. Click now to enhance your visuals!